The Social Dilemma: How to Make Social Media Platforms Safe for the Enterprise
Social media platforms are critical business channels for enterprises, but also come with major security and compliance risks. Here's how to solve them.
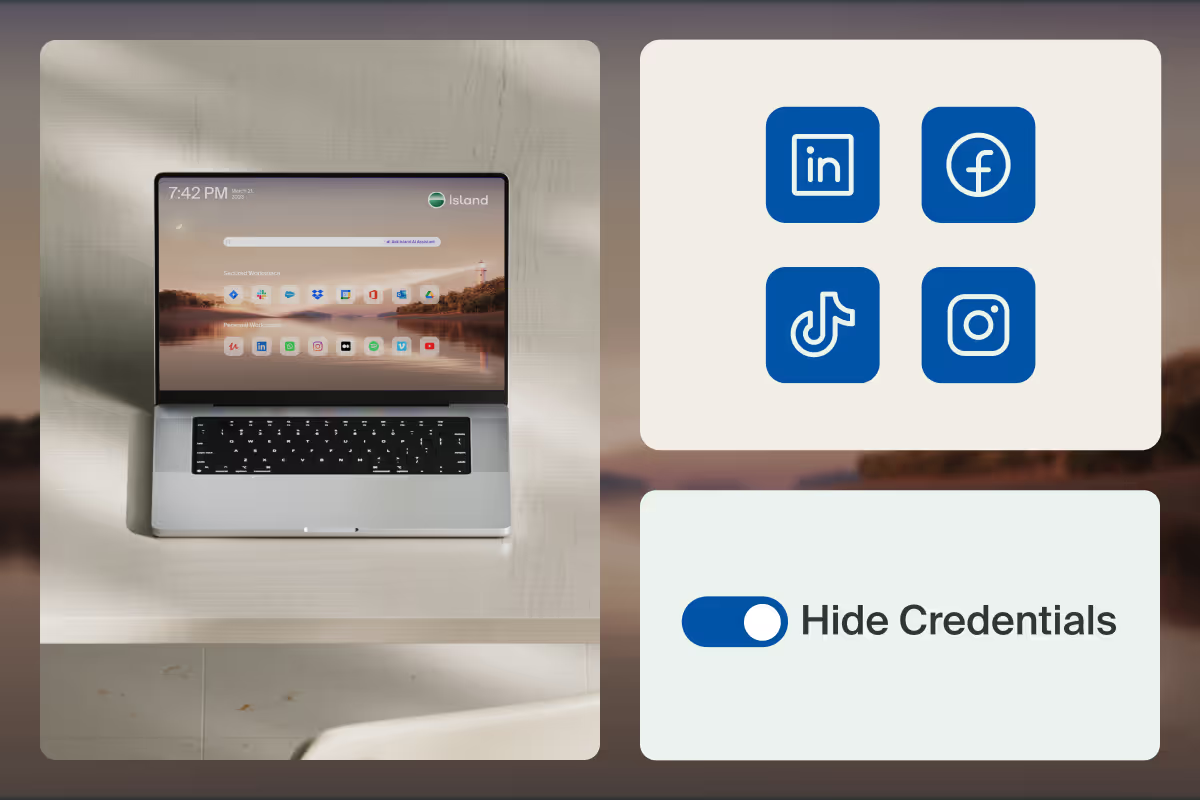
Enterprises have long embraced social media platforms as a way to directly and authentically communicate with their audiences. For many enterprises, social media is their primary marketing channel, with a significant share of revenue riding on their ability to build brand equity, engage prospects, and attract leads.
But social media platforms are also a major security and compliance headache for enterprises. Why? Because the nature of operating a company social account involves sharing credentials with internal staff and external agencies. Which causes enterprises to lose control over account access, admin privileges, and audit trails – while exposing them to serious unmitigated risk.

We’ve seen many recent stories in the news where someone with an axe to grind, an activist agenda, or simply a malicious insider uses their credentials to cause harm to the organization via the org’s official social media megaphones. Such posts even have the potential to affect the stock price of a publicly traded company.
What enterprises risk by being social
These are just some of the serious risks enterprises expose themselves to when using social media platforms:
Shared credentials expose businesses to unauthorized access and potential misuse. For example, bad actors can exploit cookie history and retrieve passwords stored in the browser, granting them unauthorized access to social media accounts and more. And phishing attacks use social engineering – such as posing as fellow employees, contractors, or even the CEO – to trick employees into revealing login credentials.
Also, failing to remove password access for departing employees is a small oversight that poses a big threat: Disgruntled or former employees can easily post on behalf of the company with little in place to stop them – as seen in recent incidents of a national car company's social account being hacked, and a leading fast food chain's account falsely announcing they’d been sold to their major competitor.
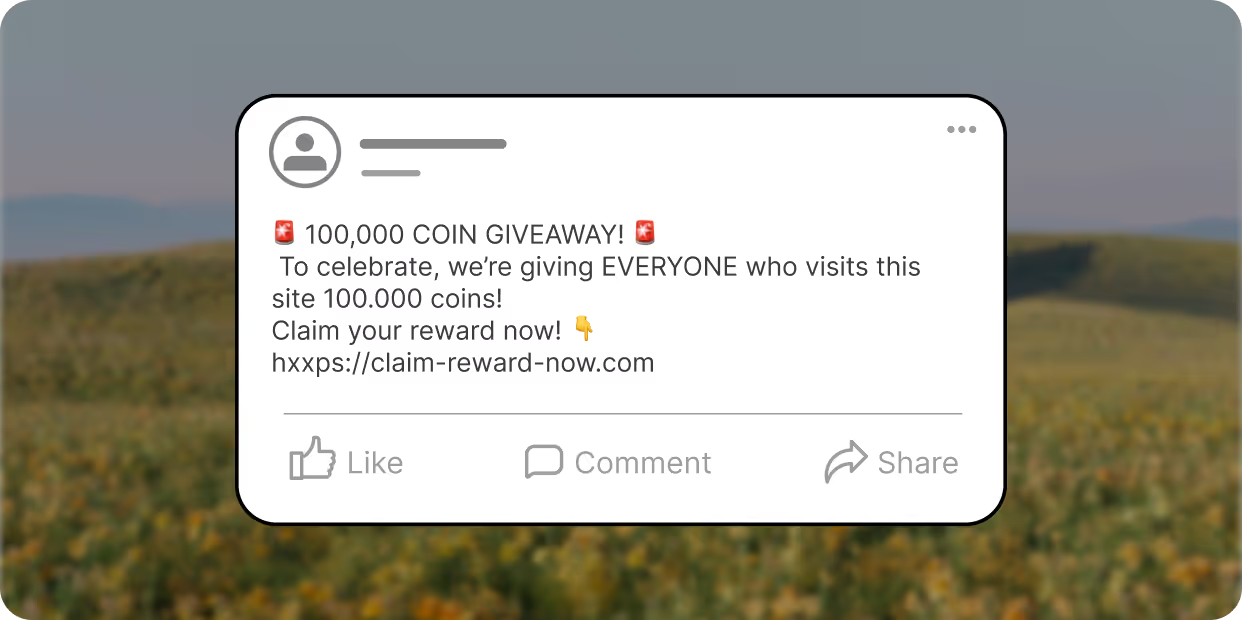
A single post can cause irreparable damage to a company’s brand and business. Without controls in place to ensure proper reviews and approvals before posting, disaster can strike at any moment. Even well-meaning posts—such as a behind-the-scenes look at company culture—can backfire if they inadvertently reveal sensitive information or violate compliance policies.
The fallout of revealing sensitive information can also include regulatory penalties and compliance violations. For example, Securities and Exchange Commission (SEC) regulations prohibit publicly traded companies from sharing material, non-public information – such as financial results or merger plans – on social media to avoid insider trading violations and compliance breaches. Such violations can have serious negative repercussions for public companies, directly influencing stock price and investor outlook.
Traditional security measures aren’t measuring up
Enterprise IT leaders have done their best to enforce safe and responsible social media use through the security tools available today. But traditional security solutions don’t have the flexibility to control specific actions or permissions inside such social media applications or even force a path of governance. They either implement overly-aggressive blunt force restrictions like blocking the social platform entirely, or insufficient protections that still leave enterprises exposed to risk. Worse yet, when such shared credentials are used, social media posts can be made from “off grid” devices ensuring there isn’t an audit path for attribution.
While this is true with any web app, this is even more pronounced with social media platforms. Because, at their core, social platforms weren’t designed to give entire teams access to company profiles. They were designed around the way individuals behave, not organizations. Which means existing governance solutions simply aren’t equipped to handle this particular situation.
But if social media platforms aren’t designed for safe enterprise use, yet they’re fundamental to its success, what’s an enterprise to do?
Securing social with the Enterprise Browser
The answer lies within the browser. The Enterprise Browser naturally embeds advanced security and granular IT controls into the browser itself, giving enterprises precise control over how users access apps and sites, interact with company data, and behave on their social media footprint – all without disrupting typical workflows. By applying company-defined policy according to the user, device, network, application, geolocation, and more, enterprises suddenly gain the security and control over social media platforms they’ve sorely lacked.

Here’s how:
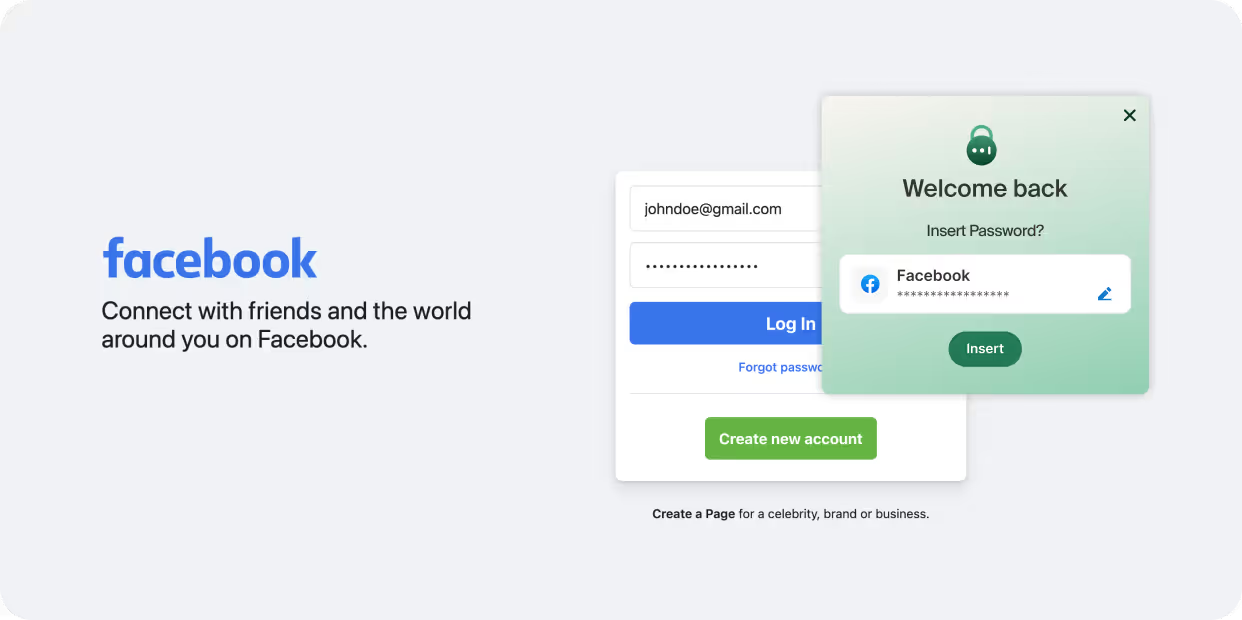
1. Privileged access management (PAM) and multi-factor authentication (MFA). The Enterprise Browser enables the organization to tightly control who accesses social media platforms, and in what way. Only authorized users are given the ability to log into the social platform to begin with, and additional authentications can be placed in front of sensitive actions, like hitting the “Publish” button, to ensure proper usage of social media at all times.
The Enterprise Browser also prevents shared passwords from falling into the wrong hands. Even when multiple users share the same account access, the browser can automatically inject credentials at the login screen so users never see the password.
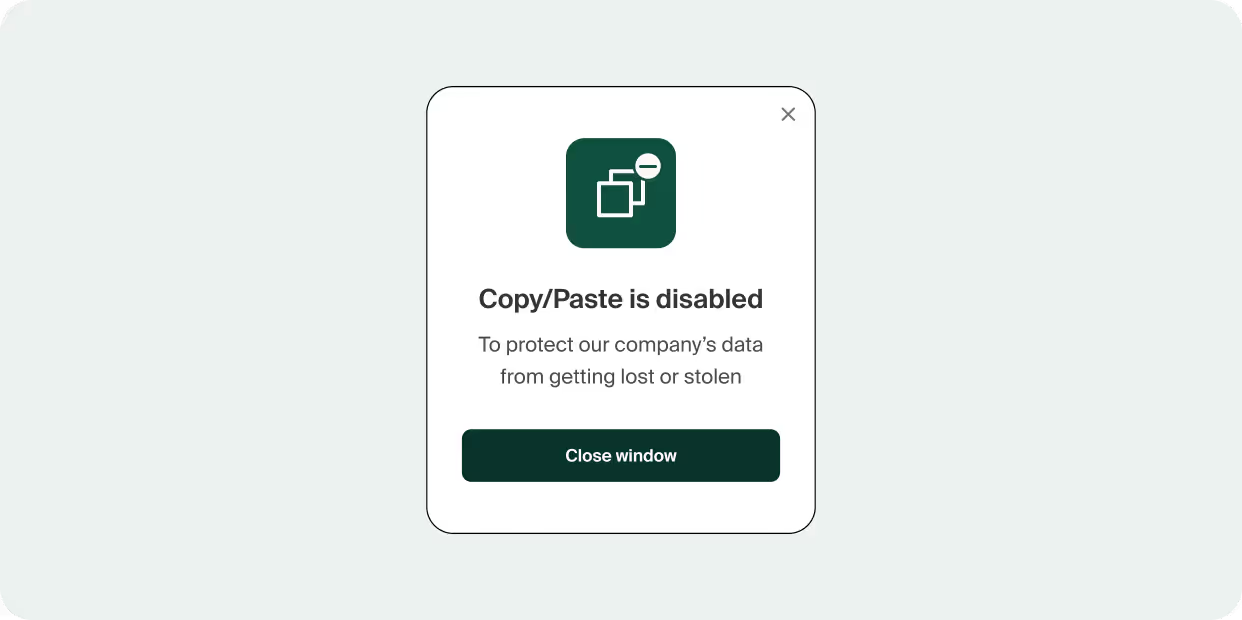
2. Last mile control data protection policies. The Enterprise Browser enables you to govern how data moves between apps and social media by controlling copy-paste, downloads, screenshots, and uploads. So for example, copy/pasting a customer quote to social from the company website will work fine. But copy/pasting a customer credit card number or material company information might be automatically blocked, by design. In addition, real-time corporate policy enforcement educates employees in the moment—not only blocking actions that violate compliance guidelines, but also explaining why, in order to minimize frustration and support tickets.
3. RPA automations. Robotic Process Automation (RPA) modules give companies the ability to customize the presentation layer of the social platform to accommodate their specific needs. For example, if an organization wanted to limit the ability to publish company social posts to the head of communications, while still giving the rest of the social team permission to reply to private messages, they can activate an RPA that removes the publish button from the user interface, when a user other than the head of communications accesses the account (yes, like magic).
%20Account%20with%20No%20Publish%20Button.avif)
4. Granular visibility. Island provides detailed visibility into all work activity down to the keystroke and mouse click, enabling IT and security teams to monitor and audit individual users’ behavior without invading their privacy. So if a post was published from a shared social account, the company can instantly see which user posted it, as well as all relevant context like device, network, location, app, etc. This means the invisibility issues caused by shared accounts are now a thing of the past. All movements and engagements can be attributed to specific people.
Making social media work for work
IT and security leaders constantly struggle with how to protect corporate assets without slowing down corporate operations. Enterprise usage of social media perfectly embodies this struggle - a key business initiative littered with serious risk. And the shortcomings of traditional security and IT solutions expose the need for a fundamentally new approach to making social safe for enterprise use.
The Island Enterprise Browser is that new approach. By embedding the core IT, security, and productivity needs directly into the browser, companies finally have the solution to social media governance—delivering the security and control enterprises require, while enabling the audience engagement they need to grow and thrive.
.svg)


.png)


.svg)
.svg)
