The Enterprise Browser Blog

6
min read
|
Aug 21, 2025
Island Partners with Cyera for a Transformational Data Security Approach
No items found.
.png)
4
min read
|
Aug 19, 2025
Illuminate Actionable Insights with Island Lighthouse
IT modernization
Enterprise security
5
min read
|
Jul 24, 2025
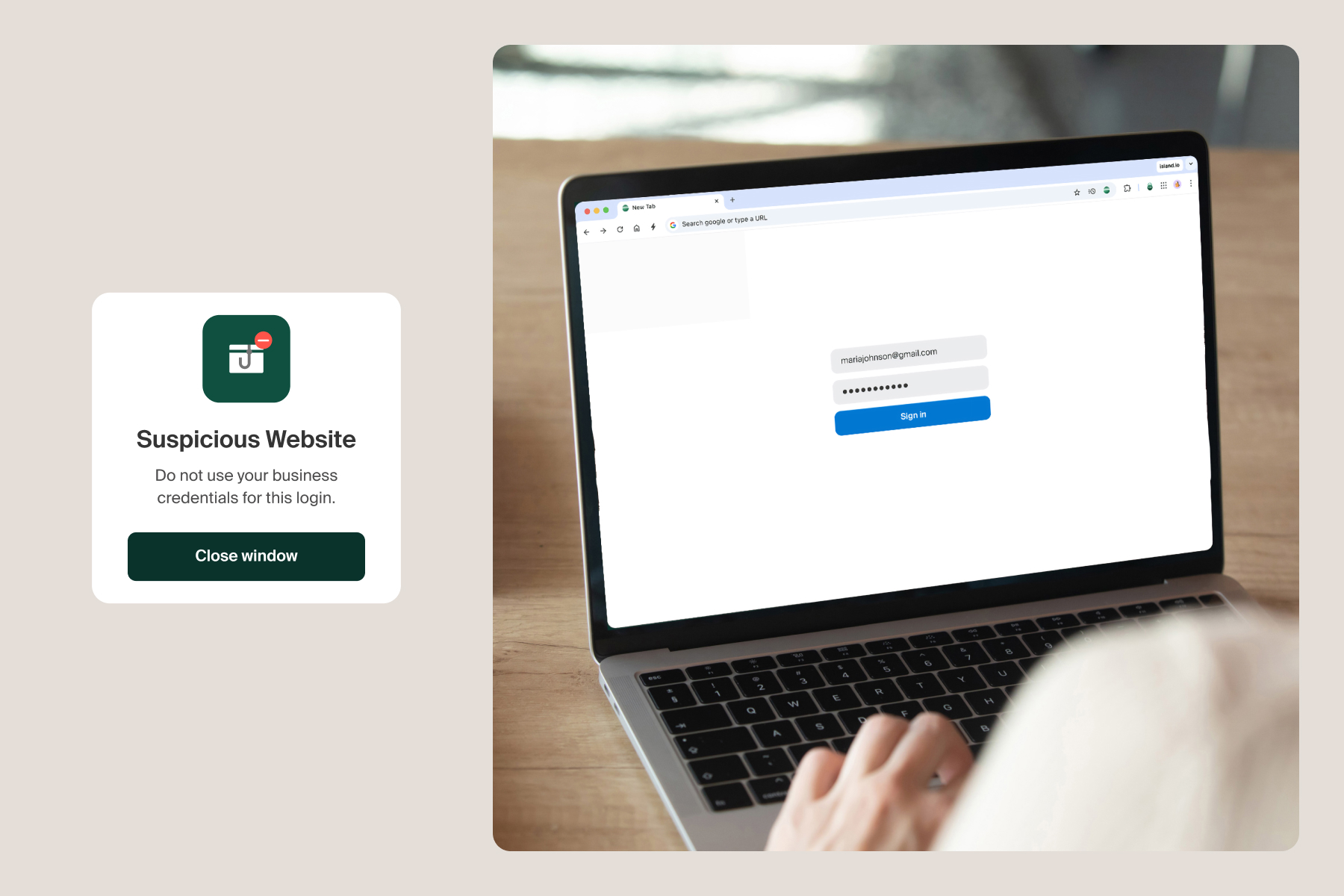
Compromised Credentials: How Enterprise Browsers Protect Access
Enterprise security
Password management
SaaS security

5
min read
|
Jun 12, 2025
TX-RAMP Level 2 Certification
No items found.

6
min read
|
May 28, 2025
How to Make Social Media Platforms Safe for the Enterprise
Enterprise security
SaaS security







.svg)
.svg)
